Protect your network from DNS hijacking
Learn about the three types of DNS hijacking, how to protect your network, and how BlueCat’s platform can further enhance your network security.

In early 2019, the U.S. government’s cybersecurity center issued a stark warning: protect your network from a DNS hijacking attack.
In this attack, the IP addresses of your domain’s DNS servers are changed to IP addresses of attacker-controlled servers. By doing so, bad actors can redirect your unsuspecting users to malicious websites.
It’s all a bit scary. But you can protect your network against it.
In this post, we’ll explore the three different methods of hijacking. Then, we’ll look at the ways you can protect your network from it. Finally, we’ll touch on how BlueCat’s platform can help further enhance your network security.
What is DNS hijacking?
DNS, or domain name system, is the phone book of the internet. It translates domain names that we easily remember, like bluecatnetworks.com, into IP addresses like 104.239.197.100, which are the language of the internet.
DNS allows computers, servers, and other networked devices, each with their unique IP addresses, to talk to each other. And it gets users to the website they’re looking for.
There are three types of hijackings:
- Attackers can compromise a domain registrar account and modify your DNS nameserver to one that they control.
- Bad actors can change the A record for your domain’s IP address to point to their address instead.
- Attackers can compromise an organization’s router and change the DNS server that automatically gets pushed down to each device when users sign on to your network.
These are sophisticated and targeted attacks. They can phish for login credentials or trick a user into clicking on a link that downloads malware. They can even sometimes display advertisements that generate revenue for the hacker.
While attackers can use different methods to compromise a network, the common thread is DNS. Don’t ignore the prospect of DNS as a threat vector. When someone controls your DNS, they can redirect users anywhere.
We should note that hijacking is not the same as DNS poisoning. Here, a bad actor intervenes in the DNS query and response process by supplying the wrong answer. This is a man-in-the-middle attack that tricks a DNS server into thinking it has found an authoritative nameserver. It’s a similar vulnerability, but it occurs at a different point in the network.
External attacks
Of the three types of attacks listed above, the first two are considered external.
In the first, which was the basis for the U.S. government alert, a bad actor compromises your domain registrar account. They modify your DNS nameserver for your domain, changing it to one they control. Each time a user queries your domain, the hacker chooses what IP address to return for the answer. As a result, users end up at any number of malicious websites.
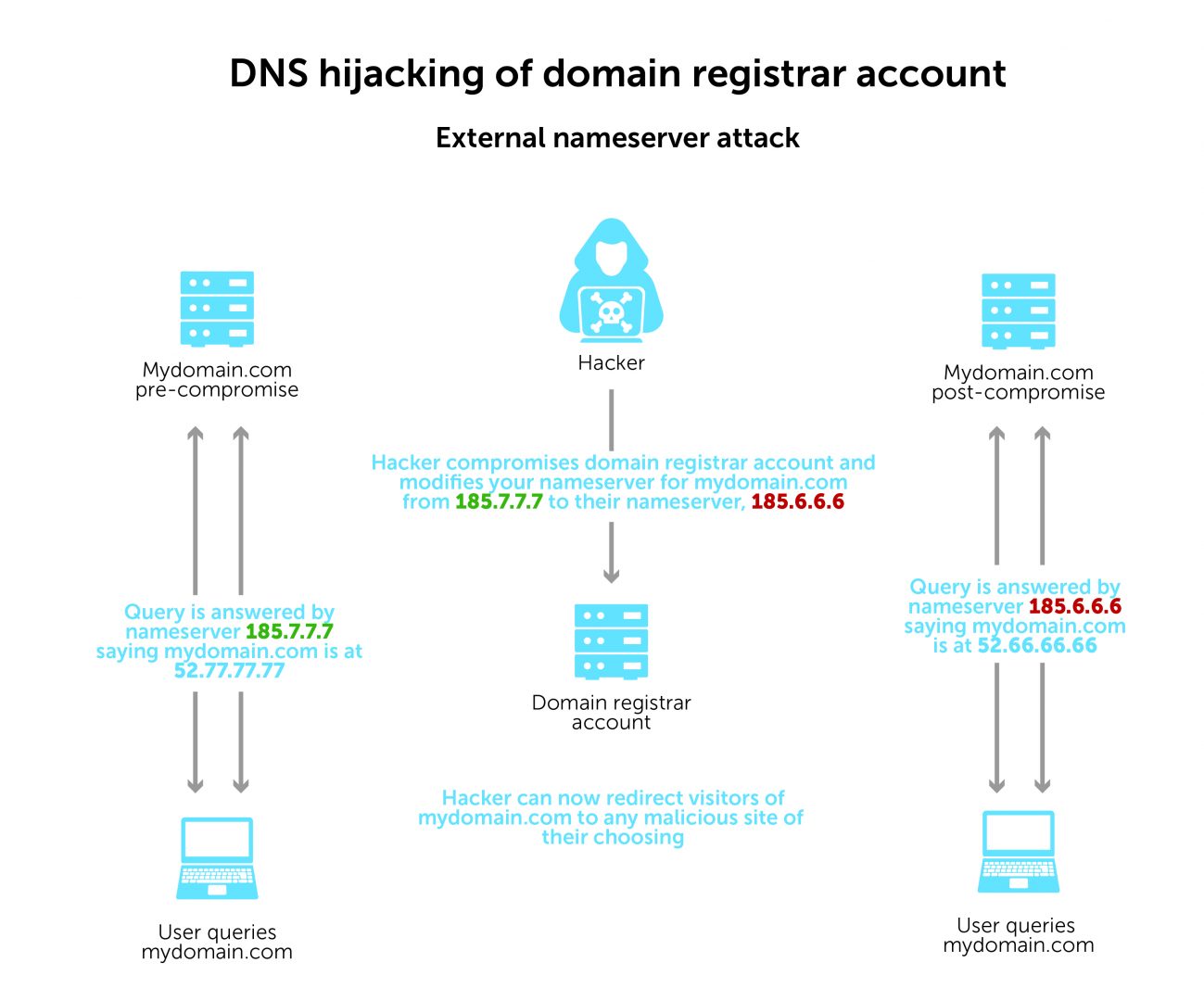
It’s a fair bit of work to implement. But this rogue DNS server setup gives the hacker a great deal of control and the flexibility to redirect users anywhere. The user has no idea they’re being sent somewhere malicious unless the website looks different from what they were expecting.
In the second type of external attack, a hacker also compromises your domain registrar account. But this time, they modify the A record for your domain. The record will point from your IP address to an IP address that they control. This always redirects users to that same IP address, every time.
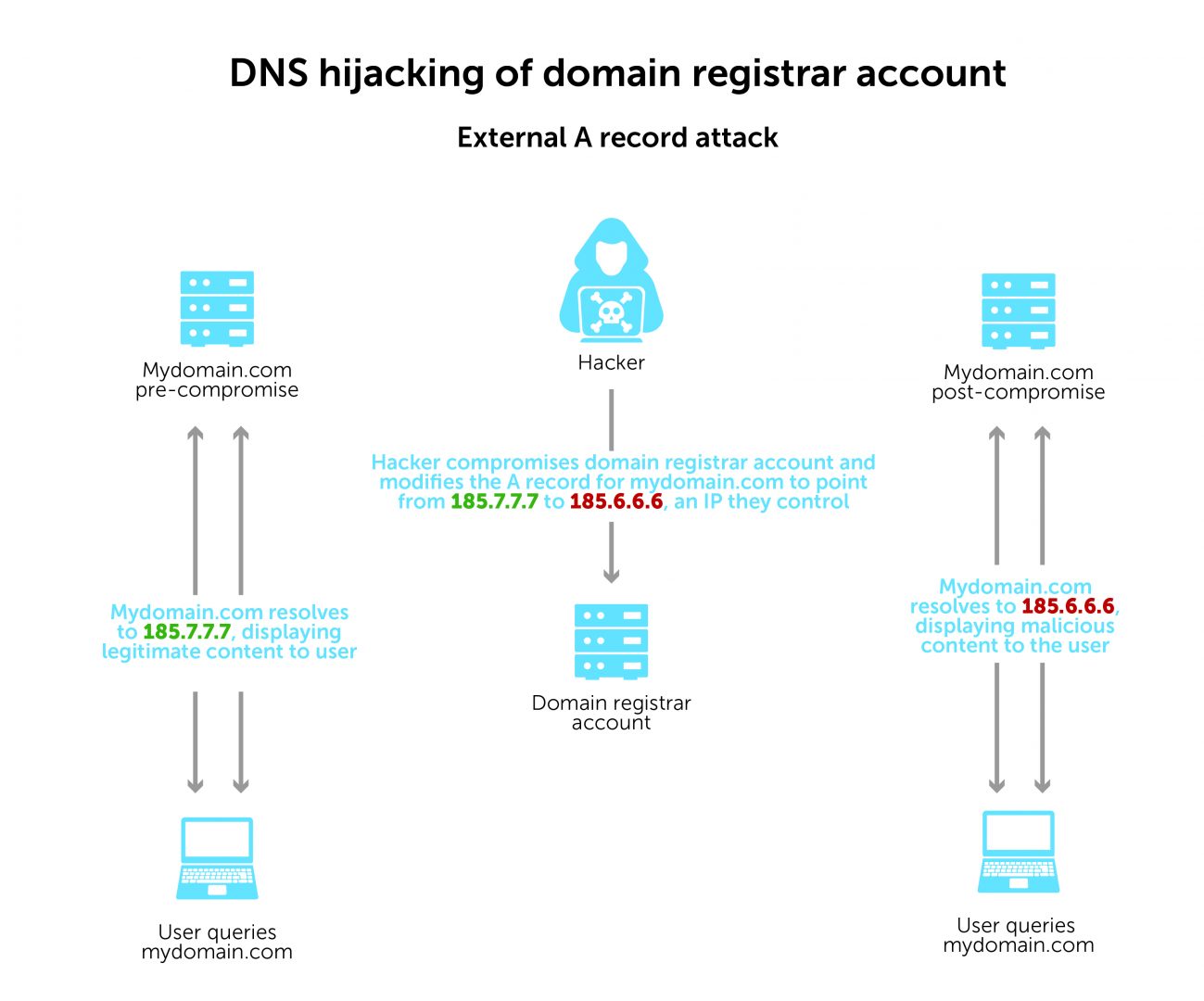
While the DNS redirection is static, it’s much easier and faster for a hacker to set up.
An example of this kind of attack is the so-called Sea Turtle incident identified by Cisco’s Talos Intelligence Group. A nation-state modified A records of national security organizations in the Middle East and North Africa in a sophisticated attempt to obtain credentials.
Furthermore, FireEye uncovered a broader DNS infrastructure hijacking campaign using both types of external attacks (including Sea Turtle). The campaign affected dozens of domains belonging to government, telecommunications, and internet service provider entities. To aid future infiltrations, attackers also obtained valid encryption certificates for the victims’ domain names.
Internal attack
Less common but still a threat is the third type, which is internal.
In a typical corporate enterprise network, routers dynamically assign devices IP addresses and DNS servers using DHCP. DNS requests, also known as queries, are directed to pre-defined resolvers to fetch responses. If a hacker gains access to the router, they can change the DHCP settings. As a result, they can tell devices to use attacker-controlled DNS servers.
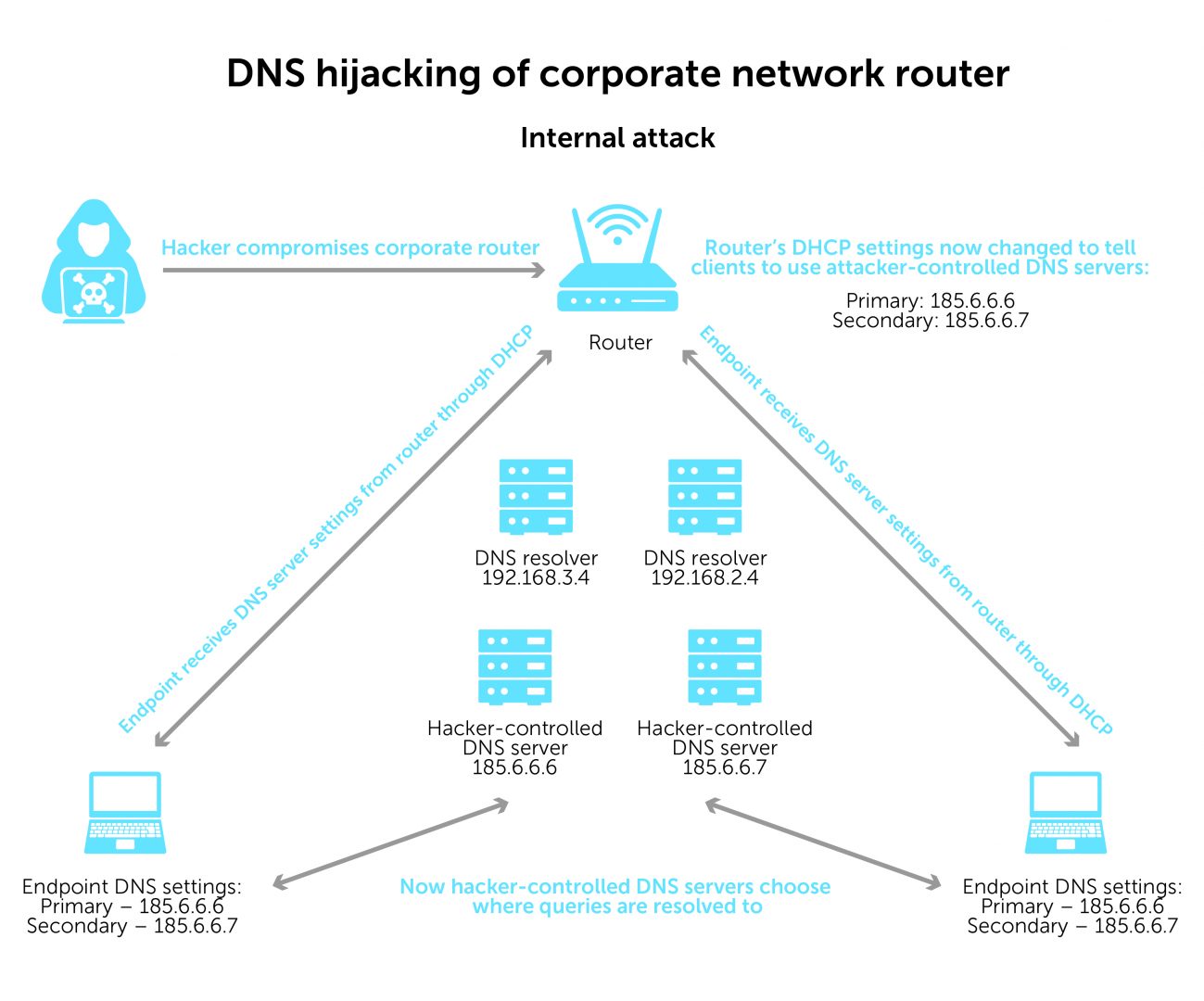
For example, if a user on your network queries Gmail.com, the hacker can redirect the user to a fake Gmail.com page. While it would look like Gmail.com, the IP address on the backend would be entirely different.
Enterprises typically secure their routers. But a bad actor can hijack DNS with a compromised router. And, even worse, they can also control all of the organization’s internet traffic.
How to protect your network from DNS hijacking
Here are some steps to take to protect your network from compromised DNS:
Monitor your DNS traffic. Detecting sophisticated attacks like these requires an equally sophisticated level of visibility into DNS traffic.
Check DNS response data, not just queries. Logging outbound queries is the first step, but ideally, you need response data as well. Examining response data patterns can identify the tell-tale signs of these types of attacks. The response will likely be different from what the originating host might have expected.
Harden your recursive DNS servers. You can protect recursive servers from unwarranted access and tampering through better architecture (including the use of DNSSEC), access controls, or physical device features.
Enable multi-factor authentication on your domain registrar account. Keep bad actors out by making it tough for them to supply all access factors.
Use a registry lock service. This sends an out-of-band notification requesting your permission before making any changes to your DNS records. Changes require authenticated contact.
Use BlueCat’s platform to keep DNS hijacking at bay
Features of BlueCat’s platform can help further protect you from network hijacking and keep attacks at bay.
Get more visibility into DNS activity patterns
A comprehensive window into DNS settings and activity with BlueCat’s platform can help you pay closer attention to data patterns. Service points collect comprehensive logs of DNS traffic, including response data. If your DNS resolvers are sending traffic to a hacker-controlled DNS server instead of your own, you’ll see a significant drop in DNS log volume.
Some customers send their DNS logs to a network Security Information and Event Management (SIEM) tool. Splunk, for example, integrates seamlessly with BlueCat. You can set an alert for this kind of anomaly with a SIEM.
Set policies to block known bad DNS servers
BlueCat’s platform gives you the ability to set policies. This includes monitoring or blocking DNS servers with bad reputations.
In our example here, the question section shows us our DNS query for bluecatnetworks.com. And in the answer section, you see the response of bluecatnetworks.com and our 104.239.197.100 IP address.
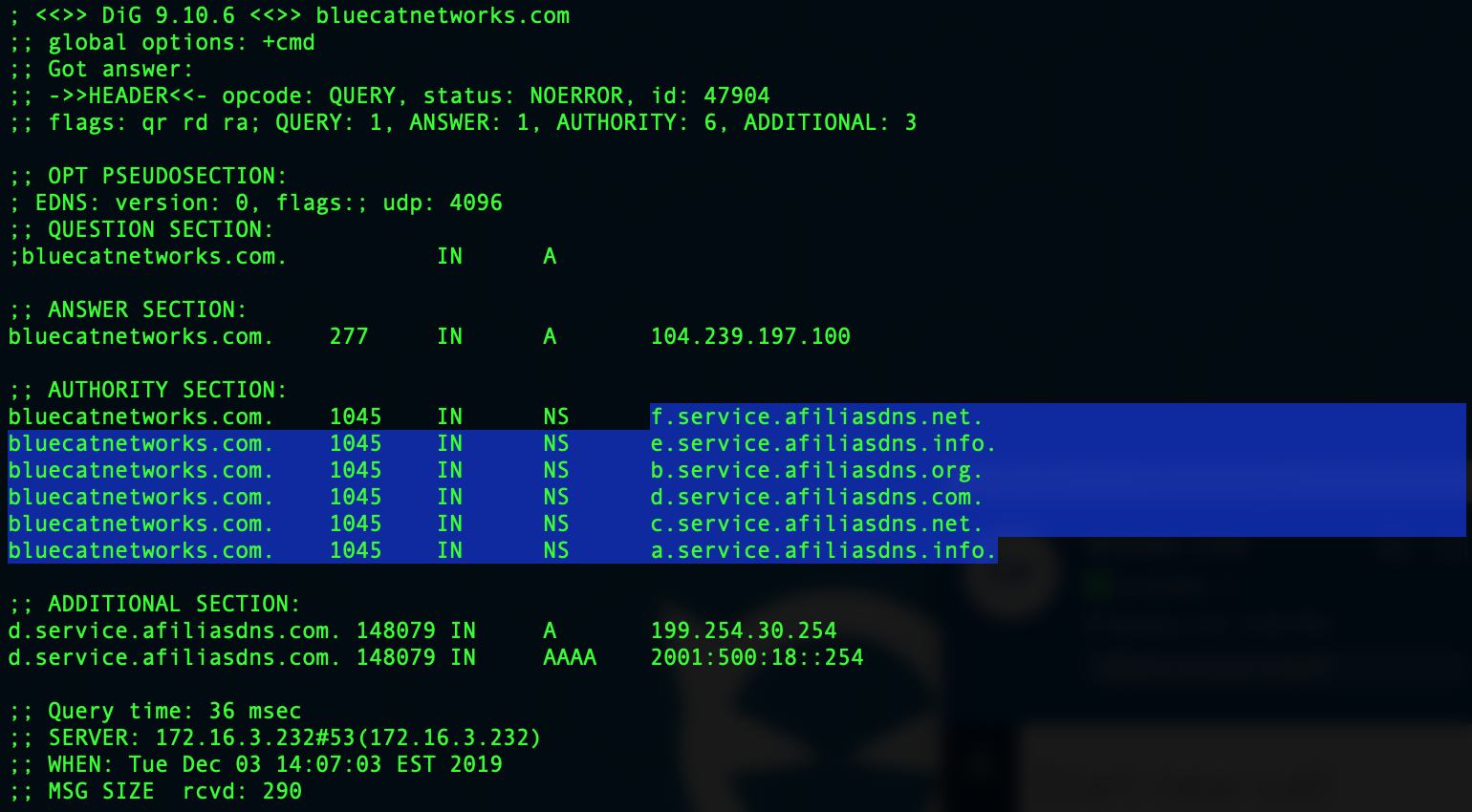
The authority section tells you which DNS server was used to resolve that query. If a hijacking occurs, those DNS servers would not be ones you’d recognize. And with BlueCat, policies can alert you if they are used or block them altogether.
Learn more about the DNS security benefits of the BlueCat platform or watch more below on how to reduce your attack surface.






