DNS over HTTPS: what, why, and who cares
Encrypting DNS queries and responses over HTTPS has long sparked robust debate, with interest from numerous stakeholders. Learn more with BlueCat.

DNS over HTTPS (DoH) has long sparked philosophical and practical debates around privacy, cybersecurity, business interests, and the state of the internet for many people.
Essentially, DoH is encrypting DNS queries and responses with HTTPS. Simple to explain, but the arguments get complicated fast.
Having trouble wrapping your head around all the DoH argument rabbit holes? Then you’ve come to the right place. The goal isn’t to sway you one way or the other, but instead to untangle the debate surrounding it.
If you wanna stir up trouble among infrastructure nerds, gather them together, and then take a position on DNS over HTTPS. Entertainment factor gets a 3x-10x multiplier when alcohol is involved.
— Ethan Banks, co-founder of Packet Pushers
This post will first examine the question of what is DNS over HTTPS. Then, it will explore some of the key arguments both for and against its implementation. Next, it will look at who some of the key players in the debate are and why they care about it. Finally, it will touch on how, if you choose, you can easily block DoH with BlueCat.
What is DNS over HTTPS?
Let’s start with the basics: the Domain Name System (DNS). Remember, DNS allows communication across devices on a network, most commonly translating human-readable domain names to computer-friendly IP addresses.
DNS works when a device asks a nearby recursive resolver a basic question: “What’s the IP address for example.com?” If that DNS resolver doesn’t immediately know with a cached answer, it asks the same question to a series of nameservers in a lookup chain until one comes up with the answer. (Or doesn’t, in the case of an IP address that doesn’t exist.)
The DNS over HTTPS protocol is simply that process of sending DNS queries and getting DNS responses but encrypted through HTTPS. As a result, those watching the hot potato of DNS requests and responses can’t tell what’s being asked.
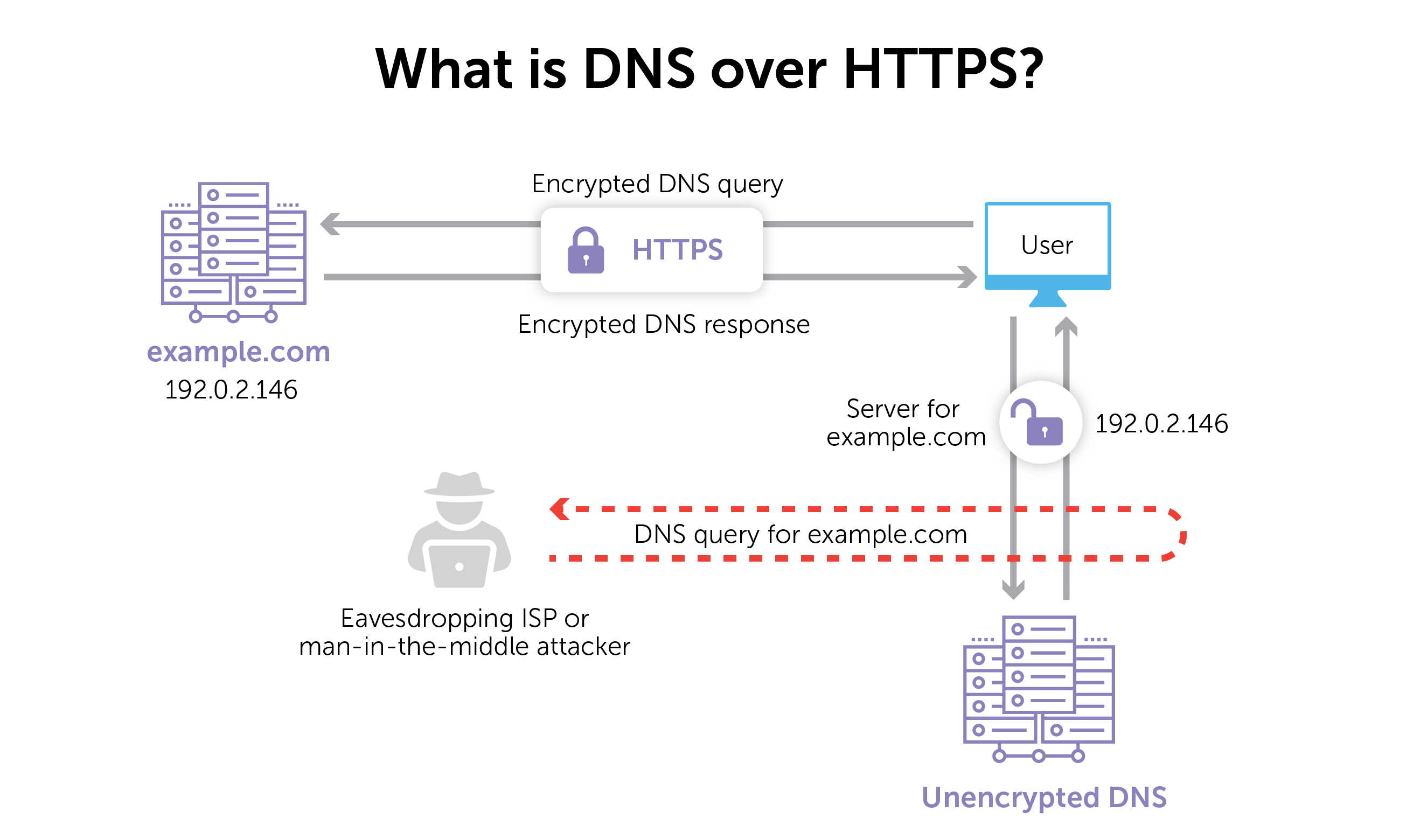
It gets far more technical than that, but that’s more or less the gist. The details are laid out in the Internet Engineering Task Force’s proposed standard RFC 8484.
There are many reasons to look at DNS queries. Network teams use the information found in DNS queries to monitor network health and contextually optimize resolution paths. Internet service providers (ISPs) are said to be watching users’ DNS queries because they signal browsing patterns. Many organizations also inspect DNS queries as part of a broader DNS security strategy for protecting networks.
The major arguments for and against DNS over HTTPS
For: “It improves user privacy”
One of the major arguments for DoH is that it protects individual users’ privacy. Encrypting DNS queries from view by ISPs and potentially prevents eavesdropping and manipulation from man-in-the-middle attacks. It’s a simple but powerful argument.
Pro-privacy organizations like the Electronic Frontier Foundation have supported DoH for this reason. For even more impassioned support, read author and blogger Cory Doctorow’s take on DoH.
Against: “Actually, it does not improve user privacy”
The quick retort to the argument above is that DoH doesn’t protect individual users’ DNS data from everybody. That’s because DoH providers (who encrypt and resolve DNS queries) still handle and see the data. In addition, there are other protocols involved in internet browsing that an ISP (or overbearing government) could use to track user browsing.
DoH encrypts precisely zero data that is not already present in unencrypted form. As it stands, using DoH only provides *additional* leaks of data. SNI, IP addresses, OCSP and remaining HTTP connections still provide the rest. It is fake privacy in 2019.
— Bert Hubert, PowerDNS founder (@bert_hu_bert) September 22, 2019
This opinion is echoed by Catalin Cimpanu on ZDNet and Maya Posch on Hackaday.
Against: “It sabotages enterprise security and network operations”
On the enterprise side, resolving DNS over HTTPS can render cybersecurity solutions blind. Many solutions rely on analyzing DNS data to protect an organization. Where organizations could once use DNS as a vector for policy-based security action they no longer can. A whitepaper from cybersecurity leader SANS details the obstacles to monitoring network traffic that organizations will face.
Furthermore, network configurations use information in a DNS query to re-route users or applications to resources based on what’s most efficient. This happens for home internet users as well. For example, some popular media companies keep servers in ISPs’ data centers. Users can resolve their queries without going all the way to the media companies’ in-house resources.
Re-routing becomes quite difficult if queries are encrypted.
DNS over HTTPS #DoH is definitely a thing. I think it will affect network security monitoring and detection in a non trivial way. #dailypcap
Pretty straight forward, but some good readings:
1) https://t.co/RnSito66aK
2) https://t.co/vDOWEHbBog
3) https://t.co/hNnvLYGKdn pic.twitter.com/AEgM5H9wui— Steve Miller (@stvemillertime) October 24, 2018
Against: “DNS over HTTPS over-centralizes the internet”
Because it is a decentralized system, DNS keeps the internet resilient. If one set of DNS servers goes down, the blast radius isn’t large.
Currently, there are only a few major public DoH resolvers. As a result, a much smaller number of servers could start resolving a larger amount of DNS traffic. In turn, the impact of an outage could theoretically affect a disproportionately larger amount of people and critical services.
Who cares about DoH?
Lots of people. Here are the key players in the DoH debate.
DNS over HTTPS providers
These are the organizations that encrypt DNS over HTTPS for internet users, including CloudFlare, Google, and Quad9. A full list of public DoH resolvers is maintained on GitHub.
Internet browsers
Internet browsers control how DNS queries flow, whether to DoH servers or otherwise. For example, since February 2020, DoH has been the default for Mozilla’s Firefox in the U.S. Firefox automatically sends DoH querying to CloudFlare’s servers for resolution. In September 2020, Google Chrome for Android began to enable DoH in a staged rollout.
ISPs
ISPs traditionally resolved (and therefore had access to) internet user DNS data before DoH. For those not using DoH, they still do. But widespread adoption of DoH has the potential to shift how they run their business. As a result, the telecommunications industry has been vocal in its opposition to DoH.
Internet users
The billions of people whose devices generate DNS queries (and therefore data to analyze) expect some privacy around their internet usage. DoH impacts that.
Important to note is that while individuals who work at enterprises also create DNS query data, they have no expectation of privacy on their employer’s network. But they’re still included in this category, as they might be unwittingly or purposely using DoH on the job.
Furthermore, some concerns have been raised that DoH will interfere with parental controls to block adult content. Mozilla is trying to address this issue by disabling DoH if it detects parental controls. It is also working with ISPs that offer parental controls to add a canary domain to their blocklists.
Enterprise cybersecurity and network teams
Cybersecurity teams ensure that enterprise network users have appropriate access to resources and that networks are secure. Meanwhile, network teams work to efficiently route DNS queries and monitor them to keep tabs on overall network health. But with encryption of DNS queries and responses, DoH changes how they do their job.
Governing bodies
The U.S. Congress and Department of Justice have scrutinized DoH. They’ve asked questions about Google’s implementation of it in Chrome in particular. That said, Mozilla alleges that lobbyists for ISPs have provided these lawmakers with inaccurate information. The company claims that the ISPs have done so to generate confusion meant to sway Congress in their favor.
Public interest groups
There are groups that both oppose and support DoH. As previously mentioned, the Electronic Frontier Foundation is a staunch DoH advocate. Meanwhile, cybersecurity consortiums like SANS have raised concerns about its unintended effects.
Others take a more neutral stance. The Encrypted DNS Deployment Initiative aims to ensure the smooth adoption and operational reliability of DNS encryption for all stakeholders.
Operating system vendors
DoH has a serious ability to impact the way DNS queries pass through operating systems. For example, in 2019, Microsoft announced DoH support for Windows. Ignoring DoH and its potential impacts on privacy and security is no longer an option, and vendors recognize that.
Blocking DNS over HTTPS with BlueCat
Enabling DNS over HTTPS is not for everyone. As previously mentioned, when it comes to cybersecurity, it reduces the visibility of DNS query activity for enterprise networks to zero. On the networking side, DoH has an impact on routing efficiency and service health monitoring. As a result, network and security admins may want to prevent users from accessing DoH services altogether.
With BlueCat’s platform, it’s easy to block DoH by adding known DoH resolvers to a response policy zone. BlueCat has long used threat feeds to bolster network defense. We’ve made it easy to block DoH with a threat feed specifically for known DoH resolvers.
To disable DoH across the enterprise, all you have to do is enable this threat feed. Learn how the BlueCat platform can help you enhance your network security.






