Splunk, DNS logs, and why DNS data matters
Interested in downloading DNS Edge for Splunk? Download it from Splunkbase.
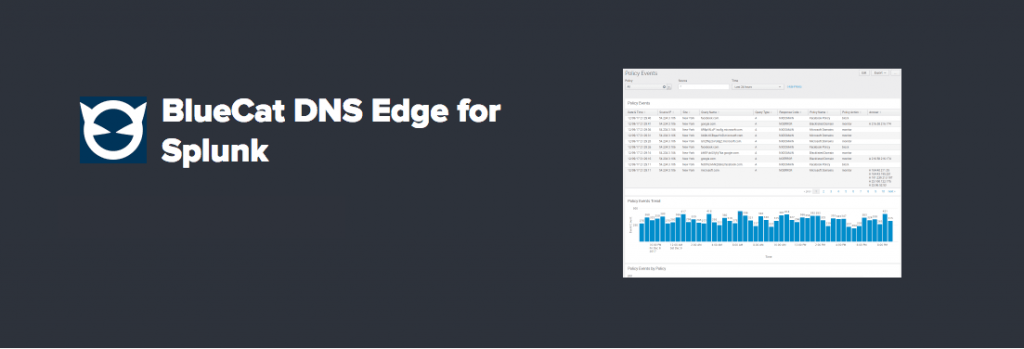
Interested in our Splunk integration? Download it from Splunkbase.
Today’s cyber security professionals and IT administrators are overwhelmed by an avalanche of data. With so many sensors and systems to monitor, the strategic vision of network security and network performance is easily lost.
Splunk provides a “single pane of glass” where IT administrators can see all their relevant DNS events and metrics of network infrastructure and security in one place. By bringing together data feeds from across the network, Splunk empowers administrators with the high-level perspectives they need to assess (and ultimately improve) system performance.
Splunk DNS logs data provides critical insights into both security and performance, yet the sheer volume of information can be difficult to digest, even in a SIEM application like Splunk. With clients and DNS servers constantly spitting out IP addresses, it takes a degree of technical savvy to capture which information is meaningful. So while it’s tempting to simply direct a raw DNS feed into Splunk, that’s hardly the way to provide actionable insight into network operations.
Putting DNS events into splunk DNS logs
With its new Splunk integration, BlueCat highlights only the refined DNS data which is directly relevant to network security and performance. On the back end, BlueCat’s powerful Intelligent Security platform does the heavy lifting, capturing DNS information at the client level. When that DNS information runs afoul of the policies set by administrators or shows signs of manipulation, it gets kicked to Splunk as an alert. Users can then apply security policies based on those alerts.
The integration between BlueCat and Splunk is seamless. Splunk customers can maintain their current instance. All the data users see in the BlueCat management screen can now be ingested into Splunk. Need to apply a policy based on a pattern of malicious activity you notice in Splunk? It’s as simple as navigating from the app to the management console. Want to add DNS data to your primary dashboard? Now you can. Looking for an alert when network activity goes against DNS policies? No problem.
If you have BlueCat Intelligent Security already, taking advantage of the Splunk app is as simple as downloading it from Splunkbase.
Analyzing DNS event logs using Splunk
Once you have the right DNS data in Splunk, it’s far simpler and faster to correlate the threat data that leads you to “patient zero”. Say your external firewall has alerted you to a malicious DNS query out on the network boundary. That information is half useful – you know something is wrong, but not where the source of the problem is.
Splunk encourages us all to “listen to your data”, and in this case DNS data is the other half of the equation. Looking at the splunk DNS logs, you can trace that query back to a source IP, look at response data, and even see the query type. This richer, granular source of information makes threat hunting much quicker and easier. As you continue to collect information and amass DNS event logs and debug logging which show patterns over time, the related insights grow deeper.
BlueCat’s integration with Splunk is part of a larger strategy to push relevant DNS data to network operations platforms that need it. On the security front, the internal, “east-west” DNS data you push from BlueCat to Splunk can also be paired with external, “north-south” data from Cisco Umbrella.
That’s a huge bounty for threat hunters, who can follow the tracks through DNS logs at multiple levels to quickly locate the source of a threat. Security teams can also use that information to build security policies, preventing future DNS-based threats from infiltrating the network and exfiltrating data.
BlueCat’s integrations with Cisco ACI and Cisco DNA center are also designed to push relevant network operation data into Splunk, creating a seamless flow between the core network infrastructure which implements policies and the higher level control plane which orchestrates the flow of data. Instead of manually collecting and compiling DNS logs, you can see them in one place and take action, optimizing your network through automation which pushes out changes across the enterprise.
Maybe you’re a Splunk customer who has always wanted to monitor DNS data, but the Microsoft DNS or BIND DNS infrastructure that you’ve got simply doesn’t allow it. If that’s the case, maybe it’s time to consider everything that BlueCat can do for you. Learn more about BlueCat Intelligent Security.






